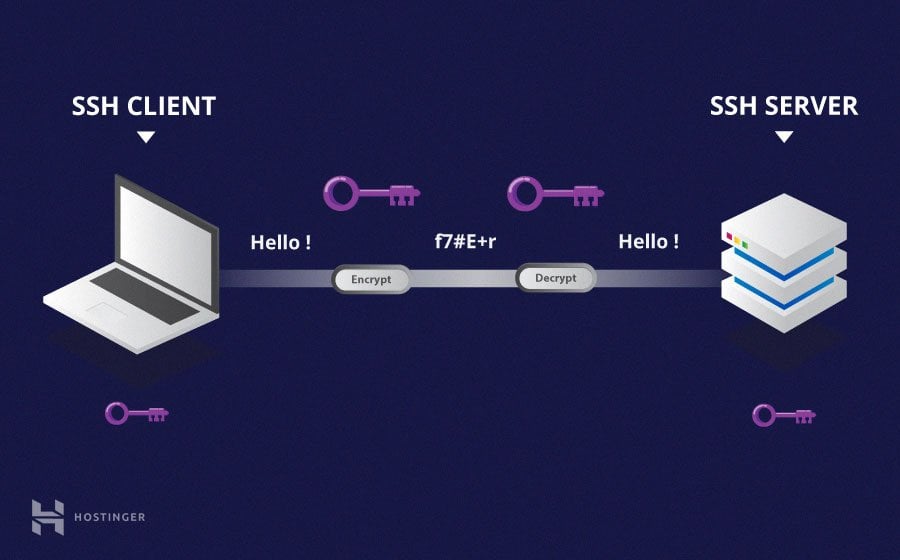
Connecting to a RemoteIoT device via SSH is a fundamental skill for anyone managing IoT systems remotely. Whether you're a developer, system administrator, or hobbyist, mastering SSH can significantly enhance your ability to manage devices securely and efficiently. In this detailed tutorial, we will explore everything you need to know about setting up, configuring, and troubleshooting SSH connections for RemoteIoT devices.
As IoT (Internet of Things) continues to grow in popularity, the need for secure and reliable remote access has become increasingly important. RemoteIoT devices are often deployed in diverse environments, making secure communication essential. This tutorial will guide you through the process of establishing an SSH connection, ensuring your data remains protected while enabling seamless control over your devices.
This guide is designed for both beginners and advanced users, providing step-by-step instructions, practical tips, and best practices to ensure a smooth experience. By the end of this article, you'll have the knowledge and tools necessary to confidently manage your RemoteIoT devices using SSH.
Table of Contents
- Introduction to RemoteIoT Device SSH
- Why SSH Is Important for RemoteIoT Devices
- Prerequisites for Setting Up SSH
- Step-by-Step SSH Setup for RemoteIoT Devices
- Securing Your SSH Connection
- Troubleshooting Common SSH Issues
- Advanced SSH Features for RemoteIoT Devices
- Best Practices for RemoteIoT Device SSH
- Real-World Applications of RemoteIoT Device SSH
- Conclusion and Next Steps
Introduction to RemoteIoT Device SSH
SSH, or Secure Shell, is a cryptographic network protocol used to securely operate network services over an unsecured network. When it comes to RemoteIoT devices, SSH provides a secure way to access and manage these devices remotely. It ensures that all communication between the client and server is encrypted, protecting sensitive data from unauthorized access.
RemoteIoT devices are often deployed in remote locations, making physical access impractical. SSH eliminates this limitation by allowing administrators to connect to the device from anywhere in the world, provided they have the necessary credentials and network access. This tutorial will walk you through the basics of SSH and how it applies to RemoteIoT devices.
Why SSH Is Important for RemoteIoT Devices
Security is a top priority when managing IoT devices. Traditional methods of remote access, such as telnet, lack the encryption and authentication mechanisms necessary to protect against cyber threats. SSH addresses these concerns by offering:
- End-to-end encryption
- Strong authentication mechanisms
- Protection against man-in-the-middle attacks
For RemoteIoT devices, SSH ensures that all commands and data exchanged between the client and server remain confidential and tamper-proof. This is particularly important in industries where IoT devices handle sensitive information, such as healthcare, finance, and industrial automation.
Prerequisites for Setting Up SSH
Before diving into the setup process, ensure you have the following prerequisites in place:
- A RemoteIoT device with SSH server capabilities
- An SSH client installed on your local machine (e.g., PuTTY for Windows or the built-in SSH client for Linux/Mac)
- A stable internet connection
- Basic knowledge of command-line interfaces
Having these prerequisites ready will streamline the setup process and help you avoid common pitfalls.
Step-by-Step SSH Setup for RemoteIoT Devices
Installing SSH Client and Server
The first step in setting up SSH for your RemoteIoT device is installing the necessary software. Most Linux-based RemoteIoT devices come with an SSH server pre-installed, but it's always a good idea to verify and update the software.
For the client side, you can use:
- Windows: Download and install PuTTY
- Mac/Linux: Use the built-in terminal application
On the server side, ensure the SSH service is running by executing the following command:
sudo service ssh start
Configuring SSH Settings
Once the SSH server is installed, you can configure its settings to meet your specific needs. The main configuration file for SSH is located at /etc/ssh/sshd_config. Here are some important settings to consider:
- Port number: Change the default port (22) to a custom port for added security
- Password authentication: Disable password authentication and use SSH keys instead
- Root login: Restrict root login to prevent unauthorized access
After making changes, restart the SSH service to apply them:
sudo service ssh restart
Securing Your SSH Connection
While SSH is inherently secure, there are additional measures you can take to further protect your RemoteIoT device:
- Use strong, unique passwords
- Implement SSH key-based authentication
- Enable firewall rules to restrict access
- Regularly update your device's firmware and software
By following these best practices, you can significantly reduce the risk of unauthorized access and ensure the integrity of your RemoteIoT device.
Troubleshooting Common SSH Issues
Even with proper setup, issues can arise when using SSH. Here are some common problems and their solutions:
- Connection refused: Ensure the SSH service is running and the correct port is open in the firewall
- Authentication failure: Double-check your username, password, or SSH key
- Timeout errors: Verify network connectivity and adjust the server's timeout settings
If the issue persists, consult the device's logs for more detailed information.
Advanced SSH Features for RemoteIoT Devices
Beyond basic connectivity, SSH offers several advanced features that can enhance your RemoteIoT device management:
- Tunneling: Create secure tunnels for transferring data between devices
- Port forwarding: Redirect traffic from one port to another for added flexibility
- File transfer: Use SCP or SFTP to securely transfer files to and from your device
These features can be particularly useful in complex IoT environments where secure communication is critical.
Best Practices for RemoteIoT Device SSH
To ensure a smooth and secure experience, follow these best practices:
- Regularly audit your SSH configuration and access logs
- Limit user access based on roles and responsibilities
- Monitor network activity for suspicious behavior
By adhering to these guidelines, you can maintain the security and reliability of your RemoteIoT device.
Real-World Applications of RemoteIoT Device SSH
SSH is widely used in various industries to manage IoT devices remotely. Some common applications include:
- Remote monitoring and control of industrial equipment
- Secure data collection from environmental sensors
- Configuration and troubleshooting of network devices
These applications demonstrate the versatility and importance of SSH in modern IoT ecosystems.
Conclusion and Next Steps
In this comprehensive tutorial, we explored the fundamentals of SSH and how it applies to RemoteIoT devices. From setup and configuration to security and advanced features, you now have the knowledge and tools necessary to manage your devices remotely with confidence.
To further enhance your skills, consider exploring the following topics:
- Advanced SSH configuration options
- Automation using SSH scripts
- Best practices for IoT device management
Don't forget to share your thoughts and experiences in the comments below. Your feedback helps us improve and provide even more valuable content. Happy learning!