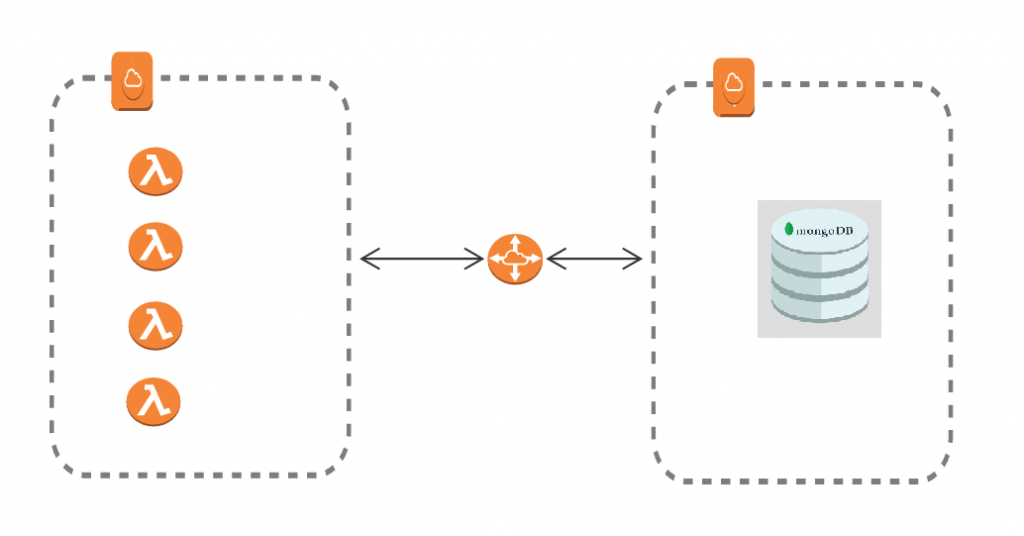
IoT SSH Tunnel AWS has become an essential solution for businesses aiming to secure their devices and networks while enabling remote access. The integration of Internet of Things (IoT) with cloud computing platforms like AWS offers unparalleled opportunities for innovation. However, ensuring secure connections is paramount in today's digital landscape. This article will delve into the intricacies of IoT SSH tunnel AWS, exploring its benefits, implementation, and best practices.
In an increasingly connected world, IoT devices are transforming industries. From smart homes to industrial automation, IoT devices collect and transmit data continuously. However, this connectivity brings security challenges. That's where IoT SSH Tunnel AWS comes into play, providing a robust solution to protect sensitive data and maintain system integrity.
This comprehensive guide will walk you through the fundamentals of IoT SSH tunnel AWS, its practical applications, and how to set it up effectively. Whether you're a beginner or an experienced professional, this article will equip you with the knowledge to leverage this technology securely and efficiently.
Table of Contents
- Introduction to IoT SSH Tunnel AWS
- Overview of IoT and Its Importance
- Understanding SSH Tunneling
- AWS Platform and Its Role in IoT
- Implementing IoT SSH Tunnel AWS
- Security Considerations for IoT SSH Tunnel AWS
- Benefits of Using IoT SSH Tunnel AWS
- Common Challenges and Solutions
- Optimizing IoT SSH Tunnel AWS
- Conclusion and Next Steps
Introduction to IoT SSH Tunnel AWS
IoT SSH Tunnel AWS represents a powerful combination of technologies designed to enhance both security and functionality. By leveraging the Secure Shell (SSH) protocol, organizations can create encrypted tunnels that safeguard communication between IoT devices and AWS cloud services.
SSH tunneling is a method of transmitting data securely over a network. When integrated with AWS, it ensures that IoT devices can communicate with cloud-based applications without exposing sensitive information to potential threats. This setup is particularly valuable for businesses operating in industries where data security is a top priority.
In this section, we will explore the foundational concepts of IoT SSH Tunnel AWS, including its architecture and key components. Understanding these elements is crucial for anyone looking to implement this solution effectively.
Overview of IoT and Its Importance
What is IoT?
The Internet of Things (IoT) refers to the network of physical objects embedded with sensors, software, and connectivity capabilities. These devices can communicate and exchange data, enabling automation and improved decision-making processes. From wearable devices to industrial machinery, IoT has revolutionized the way we interact with technology.
Why IoT Matters
- Enhances operational efficiency by automating routine tasks.
- Provides valuable insights through real-time data collection and analysis.
- Improves customer experiences by offering personalized services.
- Supports sustainability efforts by optimizing resource usage.
As IoT continues to expand, the need for secure and reliable communication channels becomes increasingly important. This is where IoT SSH Tunnel AWS plays a critical role.
Understanding SSH Tunneling
SSH tunneling is a technique used to encrypt data transmitted between two endpoints. It works by creating a secure channel through which information can flow without being intercepted or tampered with. This method is widely used in various industries to protect sensitive data and maintain privacy.
Key features of SSH tunneling include:
- Encryption of data in transit.
- Authentication of endpoints to ensure secure connections.
- Flexibility in supporting multiple protocols and applications.
By integrating SSH tunneling with AWS, organizations can achieve a higher level of security for their IoT deployments. This combination provides a robust framework for managing and protecting connected devices.
AWS Platform and Its Role in IoT
Overview of AWS IoT Services
Amazon Web Services (AWS) offers a comprehensive suite of tools and services designed to support IoT implementations. These services include:
- AWS IoT Core: A managed cloud platform for connecting and interacting with IoT devices.
- AWS IoT Device Management: A solution for organizing and monitoring IoT devices at scale.
- AWS IoT Analytics: A tool for processing and analyzing data generated by IoT devices.
Why Choose AWS for IoT?
AWS provides a scalable and reliable infrastructure that can handle the demands of IoT deployments. Its global network of data centers ensures low latency and high availability, making it an ideal choice for businesses requiring consistent performance. Additionally, AWS offers advanced security features that align with industry standards and compliance requirements.
Implementing IoT SSH Tunnel AWS
Setting up an IoT SSH Tunnel AWS involves several steps. Below is a high-level overview of the process:
- Provision AWS resources, including EC2 instances and security groups.
- Configure SSH settings to allow tunneling.
- Set up IoT devices to connect to the AWS cloud via the SSH tunnel.
- Test the connection to ensure secure and reliable communication.
Each step requires careful planning and execution to ensure optimal performance and security. Consulting AWS documentation and leveraging community resources can help streamline the implementation process.
Security Considerations for IoT SSH Tunnel AWS
Securing IoT SSH Tunnel AWS is crucial to protecting sensitive data and maintaining system integrity. Key security considerations include:
- Using strong authentication methods, such as public key infrastructure (PKI).
- Implementing network segmentation to isolate IoT devices from other systems.
- Regularly updating software and firmware to address vulnerabilities.
- Monitoring network activity for suspicious behavior.
By adhering to these best practices, organizations can significantly reduce the risk of security breaches and ensure the longevity of their IoT deployments.
Benefits of Using IoT SSH Tunnel AWS
Adopting IoT SSH Tunnel AWS offers numerous advantages, including:
- Enhanced security through encrypted communication channels.
- Improved scalability by leveraging AWS's robust infrastructure.
- Increased flexibility in managing and monitoring IoT devices.
- Cost savings through optimized resource utilization.
These benefits make IoT SSH Tunnel AWS an attractive solution for businesses seeking to maximize the value of their IoT investments while minimizing risks.
Common Challenges and Solutions
Challenges in IoT SSH Tunnel AWS
Despite its advantages, implementing IoT SSH Tunnel AWS can present challenges. Common issues include:
- Complexity in configuring and managing SSH tunnels.
- Latency concerns affecting real-time data transmission.
- Resource constraints limiting the number of supported devices.
Potential Solutions
To overcome these challenges, organizations can:
- Invest in training and development to enhance technical expertise.
- Utilize AWS tools and services to optimize performance and reduce latency.
- Plan resource allocation carefully to accommodate all connected devices.
By addressing these challenges proactively, businesses can achieve successful IoT SSH Tunnel AWS implementations.
Optimizing IoT SSH Tunnel AWS
To get the most out of IoT SSH Tunnel AWS, consider the following optimization strategies:
- Automate routine tasks using AWS Lambda functions.
- Implement data compression techniques to reduce bandwidth usage.
- Monitor system performance regularly to identify and resolve bottlenecks.
- Explore advanced features like AWS IoT Greengrass for enhanced functionality.
These strategies can help improve the efficiency and effectiveness of IoT SSH Tunnel AWS deployments, ensuring they meet business objectives and user expectations.
Conclusion and Next Steps
In conclusion, IoT SSH Tunnel AWS represents a powerful solution for securing IoT deployments and enabling remote access. By understanding its fundamental concepts, implementing best practices, and addressing common challenges, organizations can harness the full potential of this technology.
We encourage readers to:
- Share their experiences and insights in the comments section below.
- Explore related articles on our website for more information on IoT and cloud computing.
- Consider reaching out to AWS experts for guidance on implementing IoT SSH Tunnel AWS in their specific use cases.
Together, we can continue to advance the field of IoT and contribute to a more connected and secure digital future.