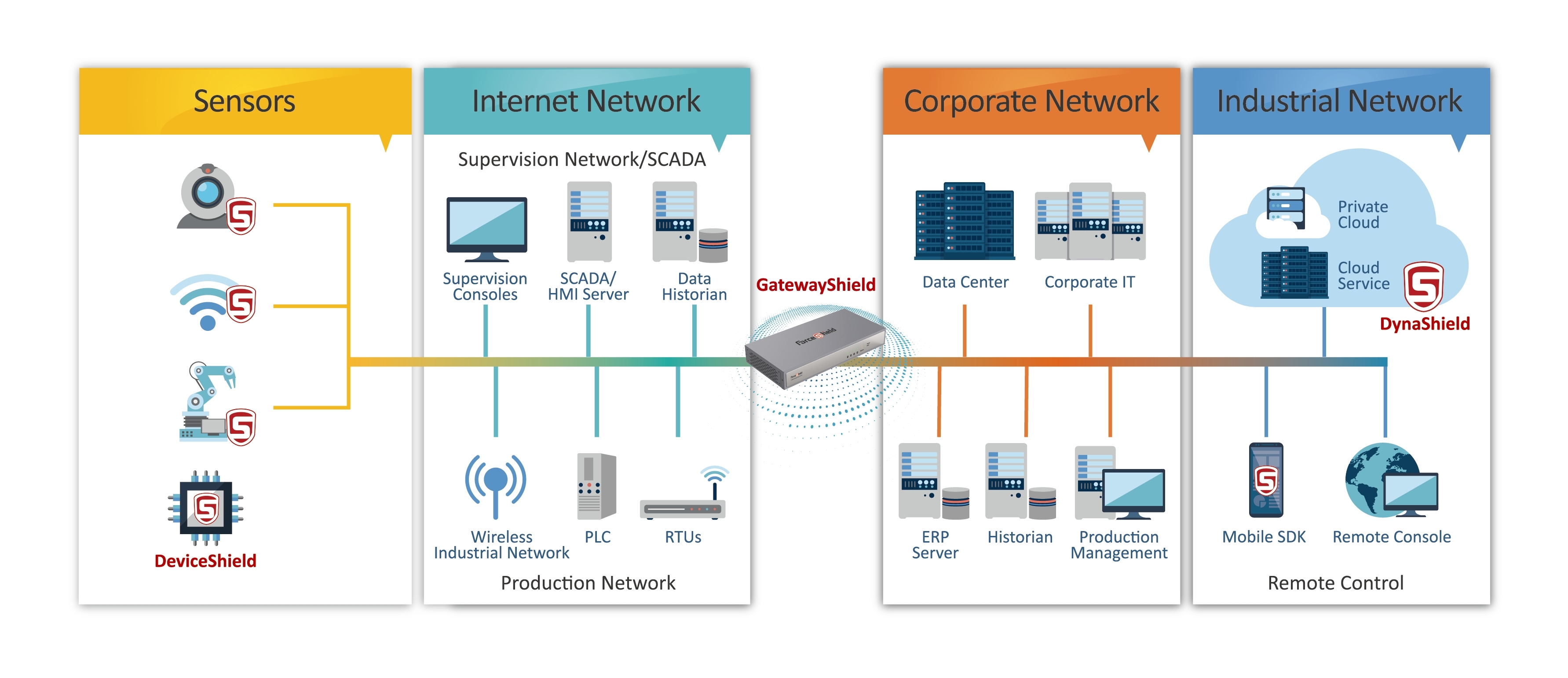
In today's interconnected world, IoT secure tunnel has become a critical component for ensuring the safety and integrity of data transmitted between devices. The Internet of Things (IoT) continues to revolutionize industries and everyday life, but with this growth comes the challenge of securing sensitive information. Understanding IoT secure tunneling is vital for anyone looking to protect their networks and devices.
As more devices become connected, the potential for cyberattacks increases exponentially. IoT secure tunnel acts as a shield, providing an encrypted and secure pathway for data to travel safely. This ensures that even if data is intercepted, it remains unreadable to unauthorized users.
Whether you're an IT professional, a business owner, or simply someone interested in IoT security, this comprehensive guide will walk you through everything you need to know about IoT secure tunneling. From its basics to advanced implementation strategies, we'll cover it all.
Table of Contents
- What is IoT Secure Tunnel?
- Importance of IoT Secure Tunnel
- How Does IoT Secure Tunnel Work?
- Types of Secure Tunnels
- Benefits of IoT Secure Tunnel
- Common Security Challenges in IoT
- Best Practices for Implementing IoT Secure Tunnel
- Real-World Applications of IoT Secure Tunnel
- Future Trends in IoT Security
- Conclusion
What is IoT Secure Tunnel?
An IoT secure tunnel refers to the process of establishing a secure communication channel between IoT devices and servers. This channel ensures that all data transmitted is encrypted and protected from unauthorized access. By creating a secure tunnel, organizations can safeguard sensitive information, such as personal data, financial transactions, and operational metrics.
Definition and Purpose
The primary purpose of IoT secure tunneling is to prevent data breaches and maintain the integrity of information. It achieves this by encrypting data packets and routing them through a secure pathway, making it nearly impossible for attackers to intercept or manipulate the data.
Key Components
- Encryption protocols
- Secure authentication mechanisms
- Data integrity checks
Importance of IoT Secure Tunnel
As IoT continues to expand, the importance of securing data cannot be overstated. With billions of connected devices, the potential for cyber threats increases significantly. IoT secure tunneling addresses these concerns by providing a robust framework for data protection.
For businesses, the implementation of secure tunnels can enhance customer trust and reduce the risk of costly data breaches. Additionally, compliance with industry regulations often requires the use of secure communication channels.
How Does IoT Secure Tunnel Work?
IoT secure tunneling operates through a combination of encryption, authentication, and secure routing. When data is transmitted between devices, it is first encrypted using advanced cryptographic algorithms. This encrypted data is then sent through a secure tunnel, which is established using protocols such as TLS (Transport Layer Security) or IPSec (Internet Protocol Security).
Step-by-Step Process
- Data encryption at the source device
- Establishment of a secure tunnel using authentication protocols
- Transmission of encrypted data through the tunnel
- Decryption of data at the destination device
Types of Secure Tunnels
There are several types of secure tunnels used in IoT environments, each with its own advantages and use cases.
TLS (Transport Layer Security)
TLS is one of the most widely used protocols for securing data transmissions. It provides end-to-end encryption and ensures the integrity of data during transit.
IPSec (Internet Protocol Security)
IPSec operates at the network layer and is commonly used in virtual private networks (VPNs). It offers strong encryption and authentication mechanisms, making it ideal for securing IoT communications.
SSH (Secure Shell)
SSH is primarily used for securing remote access to devices. While not as commonly used in IoT as TLS or IPSec, it can still provide a secure tunnel for specific applications.
Benefits of IoT Secure Tunnel
Implementing IoT secure tunneling offers numerous benefits, both for businesses and individuals. Below are some of the key advantages:
- Enhanced data security
- Improved compliance with regulations
- Increased customer trust
- Reduced risk of cyberattacks
Common Security Challenges in IoT
Despite the benefits of IoT secure tunneling, there are several challenges that organizations must address to ensure maximum security. These include:
Device Vulnerabilities
Many IoT devices are manufactured with limited security features, making them susceptible to attacks. Ensuring that all devices in a network are secure is a critical challenge.
Network Complexity
As IoT networks grow in size and complexity, managing security becomes increasingly difficult. Organizations must implement scalable solutions to address this issue.
Best Practices for Implementing IoT Secure Tunnel
To maximize the effectiveness of IoT secure tunneling, organizations should follow best practices such as:
- Regularly updating firmware and software
- Using strong authentication mechanisms
- Implementing multi-layered security measures
Real-World Applications of IoT Secure Tunnel
IoT secure tunneling is used in various industries to protect sensitive data. Some examples include:
Healthcare
In healthcare, IoT devices are used to monitor patients and transmit medical data securely. Secure tunnels ensure that this data remains confidential and protected.
Smart Cities
Smart cities rely on IoT devices for traffic management, public safety, and energy efficiency. Secure tunnels are essential for maintaining the integrity of these systems.
Future Trends in IoT Security
As technology continues to evolve, so too will the methods used to secure IoT communications. Some emerging trends include:
Quantum Cryptography
Quantum cryptography offers the potential for unbreakable encryption, providing a new level of security for IoT devices.
Artificial Intelligence
AI-powered security solutions can detect and respond to threats in real-time, enhancing the overall security of IoT networks.
Conclusion
In conclusion, IoT secure tunneling is a vital component of modern cybersecurity strategies. By understanding its importance, implementation methods, and future trends, organizations can better protect their IoT networks and data.
We encourage readers to take action by implementing secure tunneling in their own IoT systems. Feel free to leave comments or questions below, and don't forget to share this article with others who may benefit from it. For more information on IoT security, explore our other articles on this topic.
References:
- IEEE Xplore Digital Library
- National Institute of Standards and Technology (NIST)
- International Journal of Advanced Computer Science and Applications